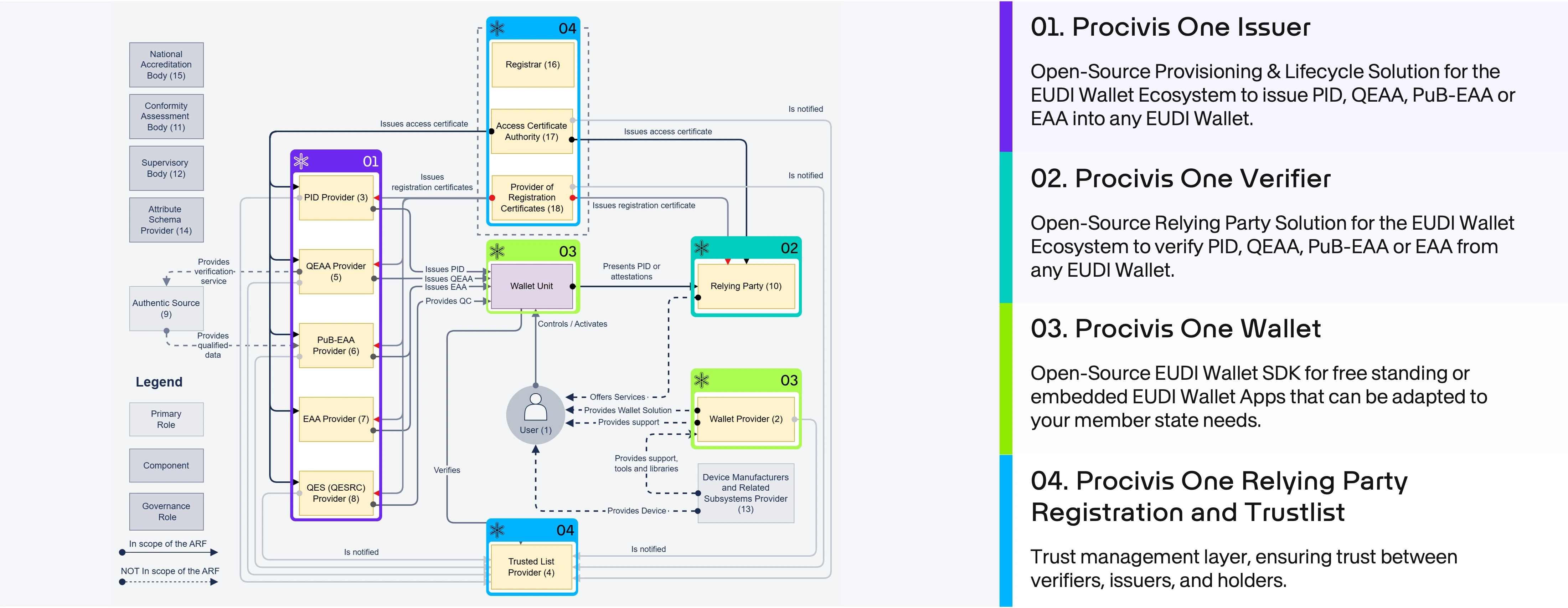
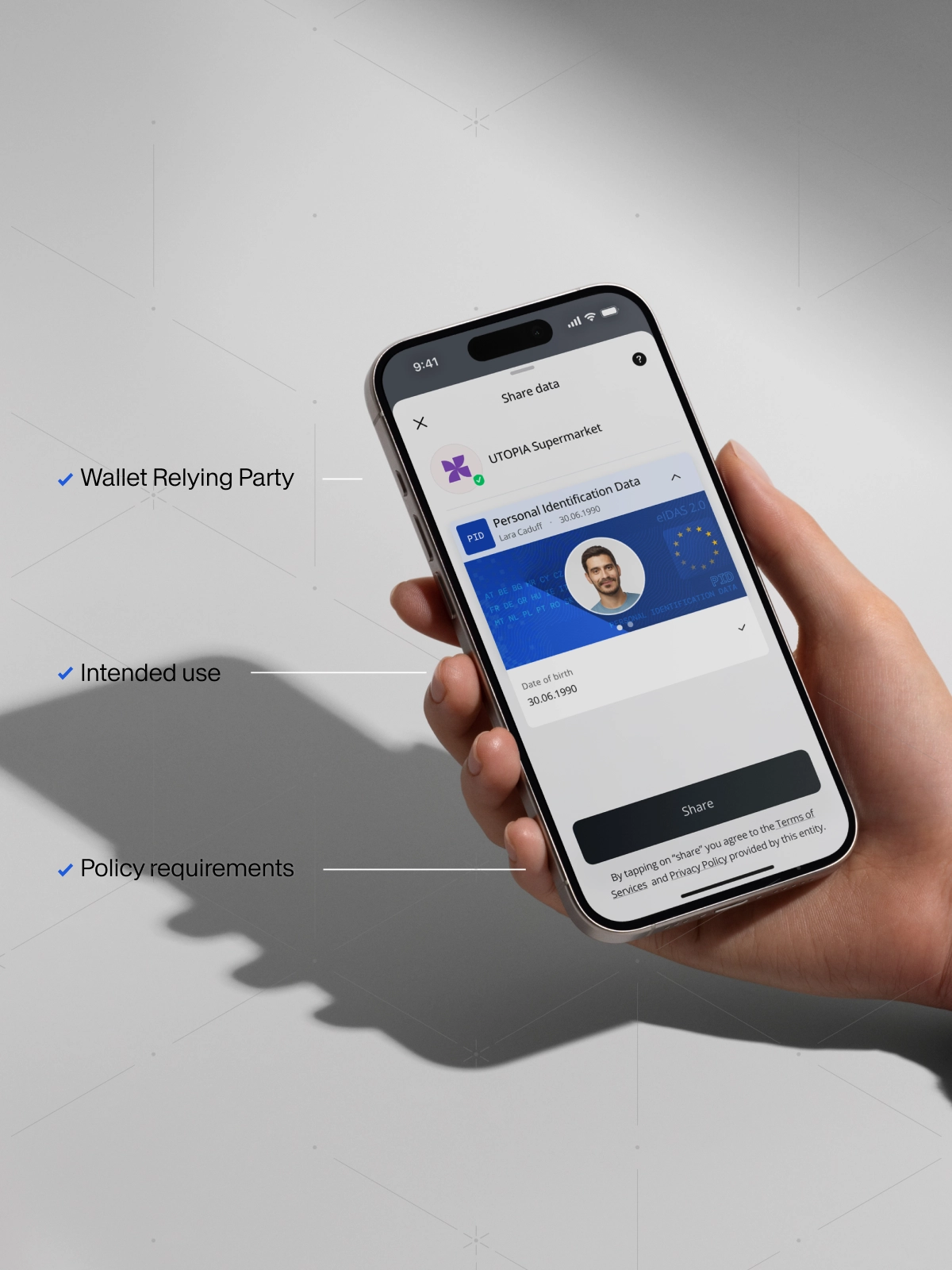
In our previous exploration of the EUDI (European Digital Identity) ecosystem, we looked at Wallet-Relying Party (WRP) registration, the mechanism that helps users trust that an organization requesting their data is legitimate and authorized to do so.
But trust in the EUDI ecosystem works both ways. It’s not only the relying party that must be verified. The wallet on the user’s smartphone and the environment it runs in must also be trusted before sensitive credentials such as a PID (Personal Identification Data) can be issued.
From an Issuer’s perspective, this means asking:
- Is this the official wallet app?
- Is it running in a supported, trustworthy environment?
- Are the cryptographic keys securely managed?
To answer these questions, the Architecture Reference Framework (ARF) defines two key attestation mechanisms implemented by the wallet provider: Wallet Instance Attestation (WIA, previously Wallet App Attestation - WAA) and Wallet Unit Attestation (WUA). Like WRP registration protects the user, WIA and WUA protect the Issuer. Together, they secure the sensitive connection between an Issuer (for example, a government authority) and a Wallet Unit (the wallet app on your phone), so credentials are only issued to a genuine, secure wallet.
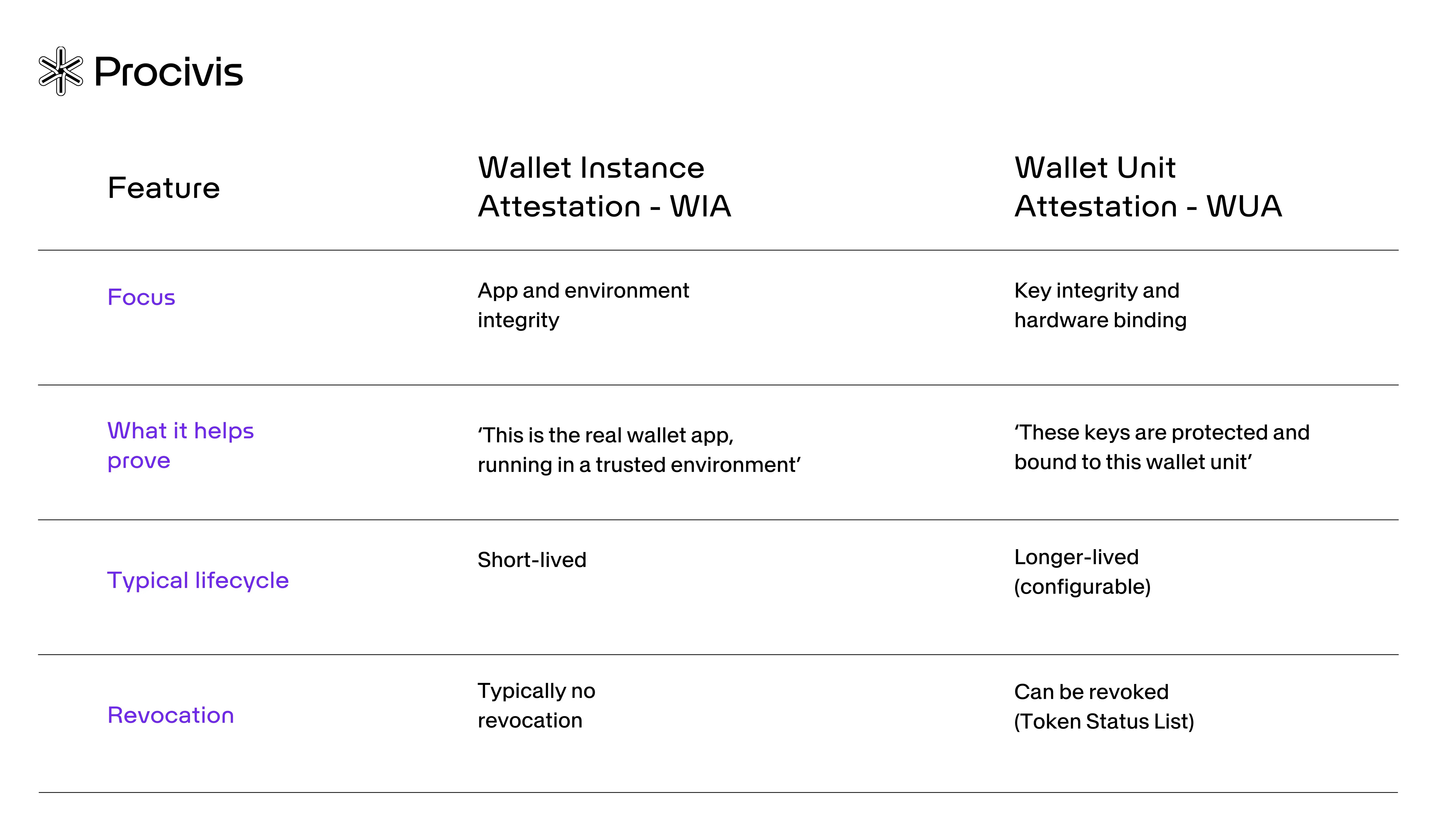
Wallet Instance Attestation (WIA): Software Integrity
Before an Issuer sends a credential, it needs to verify that the software on the other end is genuine. WIA acts as a digital seal of authenticity for the app itself.
- The goal: It attests that the app is an authentic version provided by the Wallet Provider and has not been modified
- The environment: It confirms the app is running on a supported, trustworthy device with no evidence of tampering
- Lifecycle: Typically short-lived, to reflect real-time integrity and device state
Wallet Unit Attestation (WUA): Hardware Binding
While WIA checks the software, WUA ensures that the cryptographic keys used to sign the user’s data are physically locked to the user’s specific device.
- The goal: Attests the integrity of the keys, proving they are stored in certified key-storage hardware and bound to the wallet unit (so they can’t be exported or cloned)
- What it enables: Issuers can verify security properties of the keys that credentials will be bound to (for example, secure key storage and resistance to extraction/duplication)
- Lifecycle: Longer-lived than WIA, consistent with ARF recommendations, with configurable expiration times
- Revocation: WUA can be revoked via a Token Status List if the device is lost or compromised
Why This Matters for the EUDI Wallet
While the shift to digital identity can improve convenience by reducing reliance on physical documents, the bigger driver is assurance. WIA and WUA help the EUDI ecosystem maintain high security standards by ensuring the wallet software is authentic and untampered, and that the cryptographic keys are protected in secure, device-bound hardware.
The Procivis One Advantage
Managing these complex attestation layers is a core requirement for any compliant EUDI solution. Procivis One is built to handle this complexity out of the box:
- Integrated Wallet Provider: Procivis One provides full Wallet Provider functionality, including the secure issuance and management of both WIA and WUA for its wallets
- Interoperable Issuance: When acting as an Issuer, Procivis One can seamlessly verify WIA and WUA when interfacing with other EUDI-compliant wallets
- Future-Proof Security: We ensure your infrastructure is ready for the strict security standards of the ARF, allowing you to focus on service delivery rather than cryptographic plumbing